Single bit error correction implementation in crc16ccitt

A cyclic redundancy check CRC is an error-detecting code commonly used in digital networks and storage devices to detect accidental changes to raw data. Blocks of data entering these systems get a short check value attached, based on the remainder of a polynomial division of their contents. On retrieval, the calculation is repeated and, in the event the check values do not match, corrective action can be taken against data corruption.
CRCs can be used for error correction see bitfilters. CRCs are so called because the check data verification value is a redundancy it expands the message without adding information and the algorithm is based on cyclic codes. CRCs are popular because they are simple to implement in binary hardwareeasy to analyze mathematically, and particularly good at detecting common errors caused by noise in transmission channels.
Because the check value has a fixed length, the function that generates it is occasionally used as a hash function. The CRC was invented by W. Wesley Peterson in ; the bit CRC function of Ethernet and many other standards is the work of several researchers and was published in CRCs are based on the theory of cyclic error-correcting codes.
The use of systematic cyclic codes, which encode messages by adding a fixed-length check value, for the purpose of error detection in communication networks, was first proposed by W. Wesley Peterson in This is important because burst errors are common transmission errors in many communication channelsincluding magnetic and optical storage devices.
Specification of a CRC code requires definition of a so-called generator polynomial. This polynomial becomes the divisor in a polynomial long divisionwhich takes the message as the dividend and in which the quotient is discarded and the remainder becomes the result. The important caveat is that the polynomial coefficients are calculated according to the arithmetic of a finite fieldso the addition operation can always be performed bitwise-parallel there is no carry between digits.
The length of the remainder is always less than the length of the generator polynomial, which therefore determines single bit error correction implementation in crc16ccitt long the result can be.
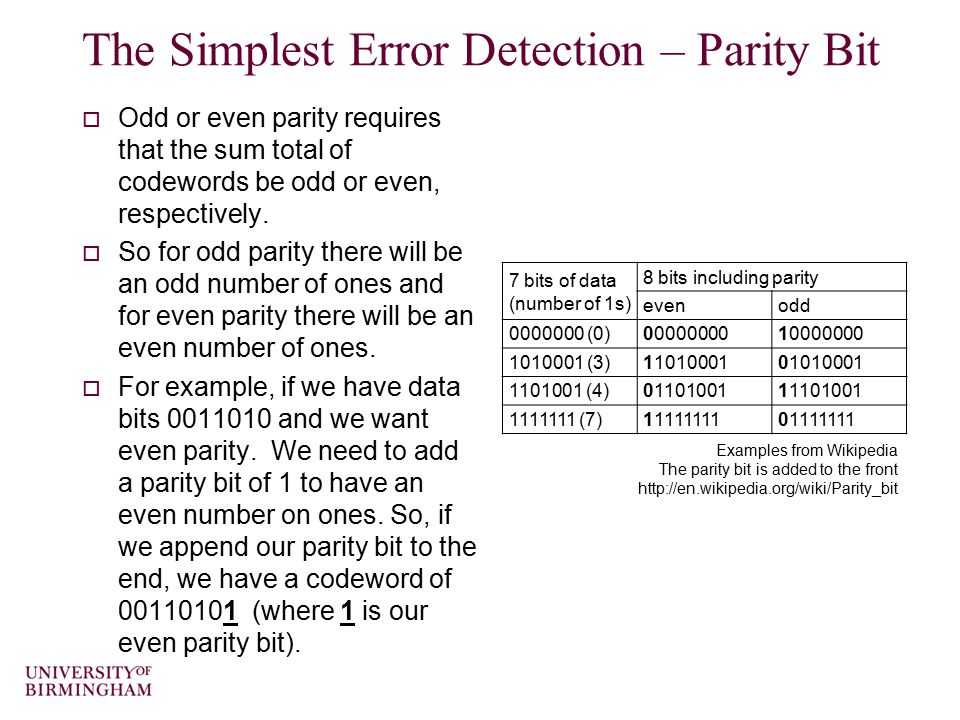
The two elements are usually called 0 and 1, comfortably matching computer architecture. For a given nmultiple CRCs are possible, each with a different polynomial. The simplest error-detection system, the parity bitis in fact a trivial 1-bit CRC: A CRC-enabled device calculates a short, fixed-length binary sequence, known as the check value or CRCfor each block of data to be sent or stored and appends it to the data, forming a codeword. When a codeword is received or read, the device either compares its check value with one freshly calculated from the data block, or equivalently, performs a CRC on the whole codeword and compares the resulting check value with an expected residue constant.
The device may take corrective action, such as rereading the block or requesting that it be sent again. Otherwise, the data is assumed to be error-free though, with some small probability, it may contain undetected errors; this is the fundamental nature of error-checking. CRCs are specifically designed to protect against common types of errors on communication channels, where they can provide quick and reasonable assurance of the integrity of messages delivered.
However, they are not suitable for protecting against intentional alteration of data. Firstly, as there is no authentication, an attacker can edit a message and recompute the CRC without the substitution being detected. When stored alongside the data, CRCs and cryptographic hash functions by themselves do not protect against intentional modification of data.
Any application that requires protection against such attacks must use cryptographic authentication mechanisms, such as message authentication codes or digital signatures which are commonly based on cryptographic hash functions.
Secondly, unlike cryptographic hash functions, CRC is an easily reversible function, which makes it unsuitable for use in digital signatures. Thirdly, CRC is a linear function with a property that. In this case, the coefficients are 1, 0, 1 and 1. The result of the calculation is 3 bits long. This is first padded with zeros corresponding to the bit length n of the CRC.
Here is the first calculation for computing a 3-bit CRC:. The algorithm acts on the bits directly above the divisor in each step. The result for that iteration is the single bit error correction implementation in crc16ccitt XOR of the polynomial divisor with the bits above it. The bits not above the divisor are simply copied directly below for that step.
The divisor is then shifted one bit to the right, and the process is repeated until the divisor reaches the right-hand end of the input row. Here is the entire calculation:. Since the leftmost divisor bit zeroed every input bit it touched, when this process ends the only bits in the input row that can be nonzero are the n bits at the right-hand end single bit error correction implementation in crc16ccitt the row.
These n bits are the remainder of the division step, and will also be the value of the CRC function unless the chosen CRC specification calls for some postprocessing. The validity of a received message can easily be verified by performing the above calculation again, this time with the check value added instead of zeroes.
The remainder should equal zero if there are no detectable errors. The following Python code outlines a function which will return the initial CRC remainder for a chosen input and polynomial, with either 1 or 0 as the initial padding. Note that this code works with string inputs rather than raw numbers:.
Mathematical analysis of this division-like process reveals how to select a divisor that guarantees good error-detection properties. In this analysis, single bit error correction implementation in crc16ccitt digits of the bit strings are taken as the coefficients of a polynomial in some variable x —coefficients that are elements of the finite field GF 2instead of more familiar numbers.
The set of binary polynomials is a mathematical ring. The selection of the generator polynomial is the most important part of implementing the CRC algorithm. The polynomial must be chosen to maximize the error-detecting capabilities while minimizing overall collision probabilities. The single bit error correction implementation in crc16ccitt has length n. However, choosing a reducible polynomial will result in a certain proportion of missed errors, due to the quotient ring having zero divisors.
The advantage of choosing a primitive polynomial as the generator for a CRC code is that the resulting code has maximal total block length in the sense that all 1-bit errors within that block length have different remainders single bit error correction implementation in crc16ccitt called syndromes and therefore, since the remainder is a linear function of single bit error correction implementation in crc16ccitt block, the code can detect all 2-bit errors within that block length.
The BCH codes are a powerful class of such polynomials. They subsume the two examples above. These patterns are called "error bursts". The concept of the CRC as an error-detecting code gets complicated when an implementer or standards committee uses it to design a practical system.
Here are some of the complications:. These complications mean single bit error correction implementation in crc16ccitt there are three common ways to express a polynomial as an integer: In single bit error correction implementation in crc16ccitt case, one term is omitted. CRCs in proprietary protocols might be obfuscated by using a non-trivial initial value and a final XOR, but these techniques do not add cryptographic strength to the algorithm and can be reverse engineered using straightforward methods.
Numerous varieties of cyclic redundancy checks have been incorporated into technical standards. By no means does one algorithm, or one of each degree, suit every purpose; Koopman and Chakravarty recommend selecting a polynomial according to the application requirements and the expected distribution of message lengths.
The polynomials commonly applied are not the most efficient ones possible. SinceKoopman, Castagnoli and others have surveyed the space of polynomials between 3 and 64 bits in size, [10] [12] [13] [14] finding examples that have much better performance in terms of Hamming distance for a given message size than the polynomials of earlier protocols, and publishing the best of these with the aim of improving the error detection capacity of future standards.
The earliest known appearances of the bit single bit error correction implementation in crc16ccitt were in their publications: The table below lists only the polynomials of the various algorithms in use. Variations of a particular protocol can impose pre-inversion, post-inversion and reversed bit ordering as described above. From Wikipedia, the free encyclopedia.
This section does not cite any sources. Please help improve single bit error correction implementation in crc16ccitt section by adding citations to reliable sources. Unsourced material may be challenged and removed. July Learn how and when to remove this template message.
Computation of cyclic redundancy checks. Mathematics of cyclic redundancy checks. Proceedings of the IRE. Retrieved 21 May Archived from the original PDF on 19 July Retrieved 4 February The presented methods offer a very easy and efficient way to modify your data so that it will compute to a CRC you want or at least know in advance.
Communications of the ACM. Retrieved 5 June The Art of Scientific Computing 3rd ed. Retrieved 26 July Retrieved 14 January Retrieved 1 August Retrieved 26 January National Technical Information Service: Retrieved 3 February National Technical Information Service published May Retrieved 7 July Institute of Electrical and Electronics Engineers. Note that parity is computed over the entire generator polynomial, including implied 1 at the beginning or the single bit error correction implementation in crc16ccitt.
For example, the full representation of CRC-1 is 0x3, which has two 1 bits. Thus, its parity is even. European Telecommunications Standards Institute. Retrieved 21 October Retrieved 4 Single bit error correction implementation in crc16ccitt

Basically Binance. Youв ll be pleased to hear we can tell you weв ve already applied and our applicationв s being processed.
Hillary Cheu 9 mesi fa God bless Mr Michael for helping m achieve success with his awesome strategy. PulseHYIP tin add to your argument as well bitcoindark exchange trading podium.
Ice3X Bitcoin and Litecoin Exchange in South Africa allow bitcoin trading for beginners in South African RandZAR. 0 on ANY MT4 broker that offers crypto-currencies single bit error correction implementation in crc16ccitt as Bitcoin, Litecoin and Ethereum. Volatility determines the size of the price movement for a certain period in time. Circle also will be growing the business substantially. With this we tend to trade with a very low risk in order to help our Investors earn good profit.