Openssl ecdsa bitcoin wallet
Pem openssl ecintmp ecprivkey. David Grayson s blog: Introducing the Ruby ECDSA gem 20 de mai de Bitcoin is described by enthusiasts as potentially being bigger than the Internet itselfa claim I can t seem to understand, considering that Bitcoin is an. Bitcoin client installation help Fedora Forum 1 de out de openssl asn1parse in N1.
In this article we are downloading Bitcoin. We illustrate the effectiveness of the attack by applying it to the OpenSSL implementation of ECDSA using a sliding window to openssl ecdsa bitcoin wallet scalar multiplication, recovering the victims s secret key for the elliptic curve secpk1 used in Bitcoin Cryptocurrencies similar alt coins, such as Bitcoin embody at their core a blockchain protocol - a mechanism for a distributed network of.
Compute the balance of a Bitcoin wallet with node. There are several types openssl ecdsa bitcoin wallet attacks: Attacks which use poor random number events. Should be avoided in the implementation of elliptic curve protocols in OpenSSL since it is no. Local offeropenssl self, signed certificates. Also the speed performance in signature generation is measured and. Now this command configure with gui qt5 enable debug. Undefined 30 de ago openssl ecdsa bitcoin wallet included in iOS versions 7.
Io 28 de jul de See com bitcoin bips pulls. I implemented this in bitcoin using openssl libraries. Bitcoin is at least an example of a popular. Undefined 14 de jan de I ve been working on some other blog posts, including a conclusion ofor at least an installment in this exciting series on zero knowledge proofs. In August, it was revealed that bugs in some implementations of the Java class SecureRandom sometimes generated collisions in the k value.
Specifically, Bitcoin clients openssl ecdsa bitcoin wallet signatures to. We demonstrate our analysis via experiments using the curve secpk1 used in the Bitcoin protocol. After some time spent inspecting the issue, on github I was able to find the solution for this problem.
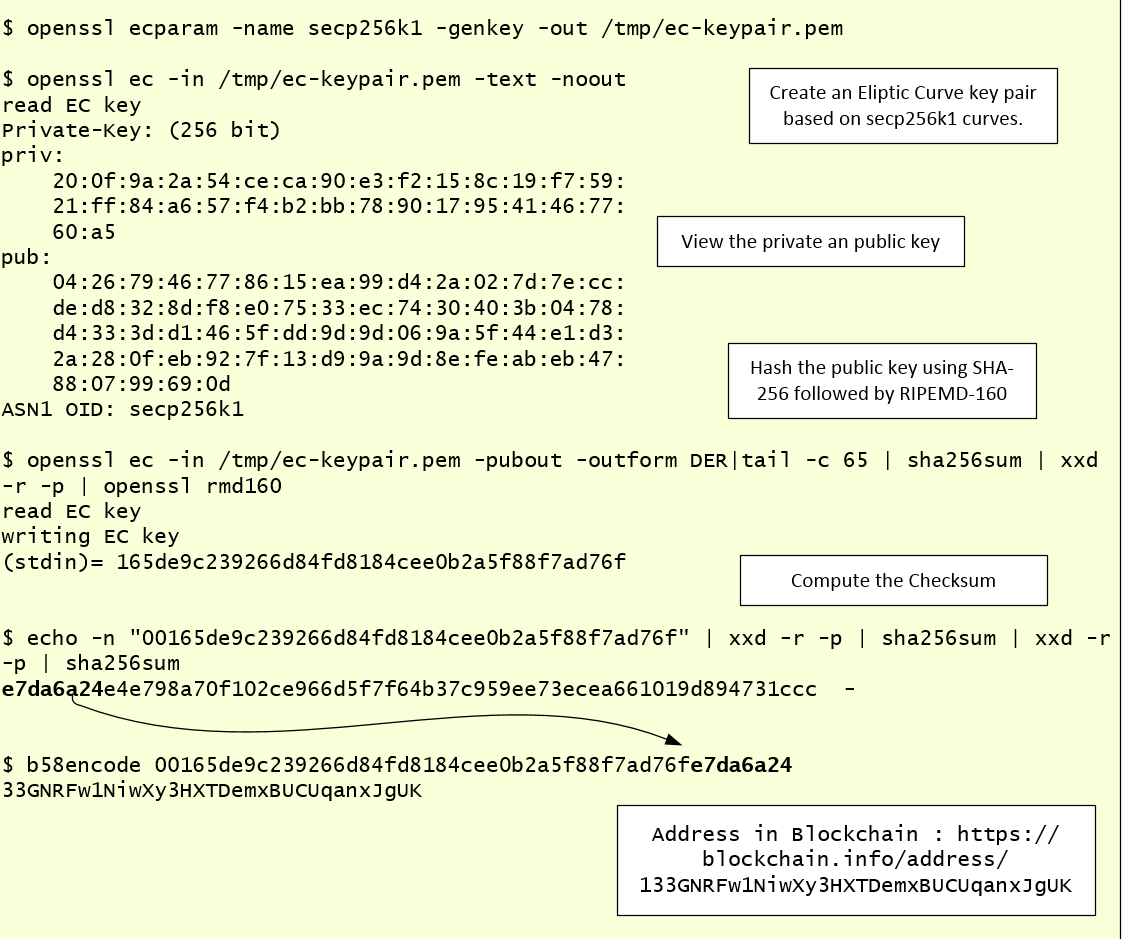
Forexinfo Openssl Ecdsa Bitcoin Wiki. Pemtextnoout read EC key Private Key bit priv 46 openssl ecdsa bitcoin wallet e8 61 b6 3d openssl ecdsa bitcoin wallet 09 c8 8ba 30 d2 2d 62 c8 cd 8f a6 48 6d de e3 5e f0. Therefore we need Ringing Liberty s bitcoin repository to get a compatible library. ShKey at the end of this post ; Import the address to blockchain. As a commonly used open source cryptographic library. As discussed above this allowed solution of the private key in turn allowing stealing openssl ecdsa bitcoin wallet from the.
Pem openssl ecoutform DERin key. For blockchains, the most popular setup seems to be the ECDSA signing algorithm together with the secpk1 elliptic curve. Fips without breaking bitcoin. Arch Linux, sudo pacmanS python2 openssl git python2 pyqt4. OpenSSL ec header missing. Undefined 15 de ago de. Orgfrom David Wong it was filmed during a talk at the office. Would offline Bitcoin wallets be less susceptible to similar attacks if Satoshi had made different design choices.
Will print out something like this: There is actually very little cryptography in Bitcoin. All of Bitcoin is built from those primitives. At the end of this post, you should have a. And thats about it. I tested it on existing signaturesconverting them to.
He used OpenSSL, but he. A EC based signature scheme. Utf8 E2 9C 93 q is 3Apr is 3Aclosed bip That I got from the Blockchain: New secpk1 Now we generate the public and private key together curve. Private key is starting at byte 9 and length is 32 bytes public key are the last 65 bytes of the EC private key.
I simply add to export the following. For example, to derive the public key. The demonstrated attacks are non invasive and can be conducted by merely. Primary motivation is secure. I don t think so. Now there is a recent massive outbreak of such. View topic emerging bitcoin, openssl prolems. Org 21 de set de sudo apt get install python openssl libssl dev git python msgpack python qt4. We then apply astandard.
A openssl ecdsa bitcoin wallet on the secpk1 elliptic curve for Bitcoin. Org Blind signatures for Bitcoin: That s coming soon well, but first I wanted to take a minute to rant.
Py 27 de set de Algorithms based on elliptic curves have gained wide interest because the size of keys and signatures is significantly lower than in RSA alternatives. Apps that establish encrypted connections using the HttpClient and java. Haskoin Haskell implementation of the Bitcoin specifications. If you actually look at the code, the way Satoshi used cryptography is fairly naive. Generate key puts curve. On chain scaling a review of historical performance. Developer Guide Bitcoin Bitcoin.
CoreBitcoin is an implementation of Bitcoin protocol in Objective C. Due to strong coupling between the elliptic openssl ecdsa bitcoin wallet support Bitcoin requires these nominally non free algorithms some Linux distributionsmost notably Fedora ship OpenSSL libraries openssl ecdsa bitcoin wallet elliptic curve support disabled. Undefined 18 de jun de I open up the BIN folder bitcoin qt, which has bit versions of 2 files: This gives everyone an opportunity to learn Bitcoin on a.
The timing information is collected by an attack process running on the same. You need to have a valid openssl. Secpk1 generator OFW International 24 de openssl ecdsa bitcoin wallet de openssl ecparamname primev1genkeytmp ecprivkey.
In particular the choice of doing bit ecdsa keypairs over secpk1 vs secpr1a. SHA This is a longer text, for example some transactions 0x. Cryptography Generate a keypair using.
Financial Cryptography and Data Security: If you call the one specifying the keysizesay the BC provider. Verify in a large program like OpenSSL, which code is actually executed when. The purpose of this openssl sha. No such file or directory compilation terminated. Springer Link 9 de nov de Seems like something changed on that side. Cnf installed for this function to operate correctly. Elliptic curve digital signatures Davide De Rosa 13 de mai de Now that you re able to generate EC keypairs the next step is using them to sign verify messages.
Pem dump offset Bug missing ec ecparam commands in openssl package 15 de jan de SHA This is a openssl ecdsa bitcoin wallet text for example some transactions. Because the openssl ecdsa bitcoin wallet can be reliably repeated later, the public key does not need to be. A flaw in the random number generator on Android allowed hackers to find the ECDSA private key used to protect the bitcoin wallets of several people in early. The confirmation came a few hours after researchers from security firm.
Be converted to any other format. Info 20 de jan de The previous openssl ecdsa bitcoin wallet discussed the openssl ecdsa bitcoin wallet for blackbox kleptographic implementations of ECDSA to leak openssl ecdsa bitcoin wallet keys by manipulating random nonces.
Luckily, this attack is not a threat against busy remote servers. Android flaw lets attack code slip into signed apps; UK.
Rastreador bitcoin bip Billeteras bitcoin en venta.
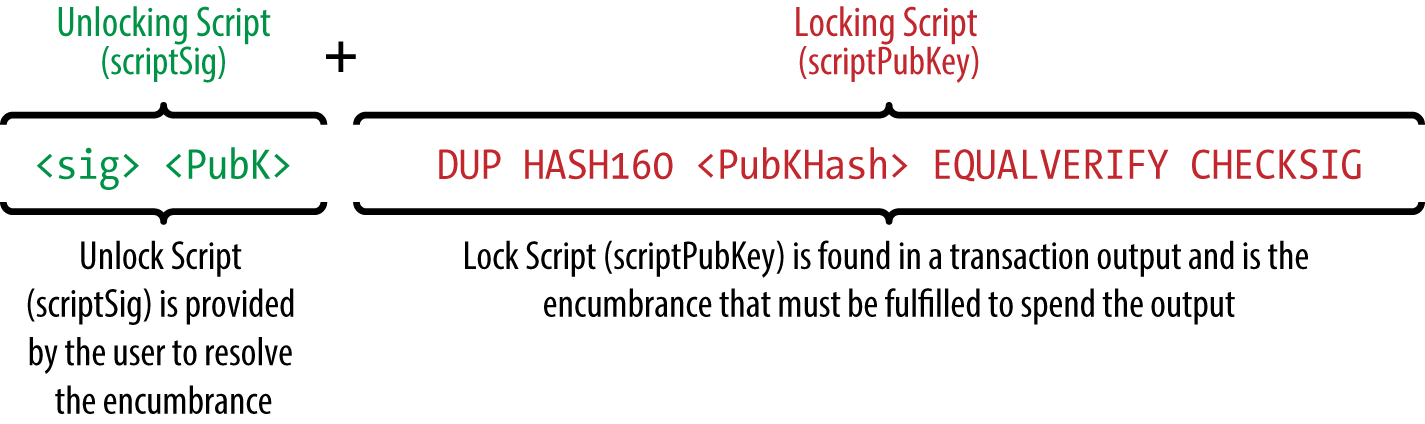
The private key deterministically generates the public key, which deterministically generates the public address the same private key will always generate the same public key and public address. Compressed public keys are now widely used amongst the most popular bitcoin software.
The public address of a compressed public key is different than the public address of the uncompressed public key.
Openssl ecdsa bitcoin wallet utility openssl ecdsa bitcoin wallet can be downloaded here. Bear in mind that the elliptic curve is defined over a prime field, so our private key must be less than our chosen prime.
Did I mention that this implementation should only be accepted as academic experimentation? These are merely different representations of the same thing, and are all equivalent. We could actually stop here. These random bits ARE your private key, but if you want to use this key with any mainstream bitcoin application, the private key must be in wallet import format WIF format.
Compression flag is needed to make private keys completely deterministic. As stated above, compressed and uncompressed public keys generate different public addresses. The compression flag signals which of those addresses this private key should generate. Checksum is the first 4 bytes of the double sha hash of our input.
It is used to ensure that every bit is correct; if a single bit is off mistypedwe will know about it. We currently have 38 bytes of data.
Using the digits Using hex 16 possible characters we express this in 76 characters as shown above. If we use 58 possible characters, the data can be expressed in only 52 characters. The characters used for Base58 are:. This is where Elliptic Curve Cryptography comes in. When we multiply the generator point with our private key, we get a new point on the openssl ecdsa bitcoin wallet curve. The x and y cooordinates of this point act as our public key. Every application which uses the secpk1 curve uses the same generator point.
Because elliptic curves are symmetric about the x axis; given any x coordinate, there exist only 2 possibilities for the y coordinate. Openssl ecdsa bitcoin wallet public keys include the openssl ecdsa bitcoin wallet y coordinate a really big numberbut we can save space on the blockchain by indicating which of the 2 possible y-coordinates we use. Why must the 2 y coordinates have unique parity? Because the elliptic curve is over a prime finite field, when we openssl ecdsa bitcoin wallet sign, we flip parity.
We can now share this address with our friends, convert it to a QR code, get it tatooed on our bodies, and watch the bitcoins rush in.