Bitcoin virus attack
On the downside, the password-changing process would potentially take much longer, cost a transaction fee or more, and - intially at least - the new wallet is no longer backed up. On the upside, non-technical users won't find their wallets drained from security compromises they believed they had closed, nor be required to locate existing backups of a wallet in order to destroy them.
Tracing a coin's history can be used to connect identities to addresses the Anonymity article elaborates on this concern in greater detail. If an attacker attempts to fill the network with clients that they control, you would then be very likely to connect only to attacker nodes.
Although Bitcoin never uses a count of nodes for anything, completely isolating a node from the honest network can be helpful in the execution of other attacks. Incoming connections are unlimited and unregulated, but this is generally only a problem in the anonymity case where you're probably already unable to accept incoming connections.
Someone who can see all of your Internet traffic can easily see when you send a transaction that you didn't receive which suggests you originated it. Bitcoin-QT has good Tor integration which closes this attack vector if used. Sending lots of data to a node may make it so busy it cannot process normal Bitcoin transactions.
Bitcoin has some denial-of-service prevention built-in, but is likely still vulnerable to more sophisticated denial-of-service attacks. These are the current Bitcoin Satoshi client protections to deter DoS attacks, as of version 0. See Timejacking for a description of this attack. It can be fixed by changing how nodes calculate the current time. Since arbitrary data can be included in Bitcoin transactions, and full Bitcoin nodes must normally have a copy of all unspent transactions, this could cause legal problems.
However, Local node policy generally doesn't permit arbitrary data transactions attempting to embed data are non-standard , but steganographic embedding can still be used though this generally limits storage to small amounts. Various ideas have been proposed to further limit data storage in the UTXO set but are not currently being seriously considered for deployment.
It's possible but unlikely that a newly discovered bug or security vulnerability in the standard client could lead to a block chain split, or the need for every node to upgrade in a short time period. For example, a single malformed message tailored to exploit a specific vulnerability, when spread from node to node, could cause the whole network to shutdown in a few hours. Bugs that break user anonymity, on the contrary, have been found, since the pseudo-anonymity property of Bitcoin has been analyzed less.
Starting from version 0. The security critical sections of the source code are updated less and less frequently and those parts have been reviewed by many computer security experts. Also Bitcoin Satoshi client has passed the test of being on-line for more than 3 years, without a single vulnerability being exploited in the wild.
See Common Vulnerabilities and Exposures for a detailed list of vulnerabilities detected and fixed. Energy consumption for mining has a high correlation with bitcoin value exchange rate. Because variable costs of mining are dominated by electricity price, the economic equilibrium for the mining rate is reached when global electricity costs for mining approximate the value of mining reward plus transaction fees. So the higher the value of one bitcoin, the higher the value of mining rewards and transaction fees, the higher the energy consumption of the bitcoin network in the long run.
If that happens, Bitcoin can shift to a stronger algorithm. Bitcoin can easily scale beyond the level of traffic VISA sees globally today. See the discussion on the scalability page for more information.
If there is even a "trickle" of a connection between two sides of a segmented network, things should still work perfectly. Then generations will start to mature, and any transactions based on those generations will become invalid when recombined with the longer chain.
The IP addresses of most users are totally public. You can use Tor to hide this, but the network won't work if everyone does this. Bitcoin requires that some country is still free. Nodes that generate blocks can choose not to include a transaction in their blocks. When this happens, the transaction remains "active" and can be included in a later block. Two things discourage this:. This allows him to:. Note that the above limitations only apply to the perspective of Bitcoin as seen by full nodes.
Some lightweight nodes work by trusting miners absolutely; from the perspective of Bitcoin as seen by lightweight nodes, miners can steal BTC, etc. This is one of the reasons why lightweight nodes are less secure than full nodes. It's much more difficult to change historical blocks, and it becomes exponentially more difficult the further back you go.
As above, changing historical blocks only allows you to exclude and change the ordering of transactions. If miners rewrite historical blocks too far back, then full nodes with pruning enabled will be unable to continue, and will shut down; the network situation would then probably need to be untangled manually eg.
The imposition of refereeing technology has created a myth of decision-making infallibility, shown up by the video assistant referee's A-League grand final glitch, writes Richard Hinds. Animal hospitals and carers are seeing more emaciated koalas, possums with dog bites and wallabies hit by cars than ever before. The Petya cyber attack hit Australian businesses. Global ransomware attack affects Australian workers. So you've been hacked.
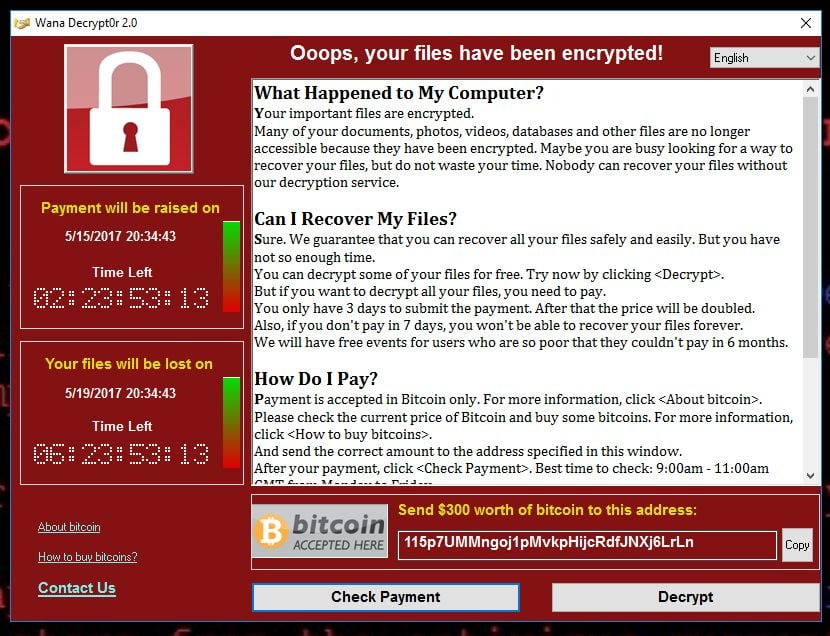
Here's what to do next. A cyber attack could cause the next global financial crisis. The attack first shut down operations in Russia and Ukraine before going global Experts are scrambling to determine the scope and impact of the attacks It is believed the latest attack might be a ransomware virus called Petya. Hackers have asked to be paid in Bitcoin. Companies and government agencies confirmed to be affected: Russia's largest oil company, partly state-owned Ukraine: Netherlands-based transport company AP Moller-Maersk: Ransomware attack comes to Tasmania.
This is what Cadbury's Hobart computers look like since 9: China retaliates after US slams territory warning to international airlines Mystery over fate of sky-diving princess 'missing after trying to flee Dubai' Vladimir Putin sworn in for another six years as Russian President Mystery of hidden room in King Tutankhamun's tomb put to rest Hawaii volcano destroys 26 homes, blasts lava more than 60 metres into the air Opinion: Minister promises body modification crackdown.
Connect with ABC News. Got a news tip? Editorial Policies Read about our editorial guiding principles and the enforceable standard our journalists follow. Cemeteries' new role By Connie Agius Would you have coffee in a cemetery or take your kids to play near a family member's final resting place? Debt and deficit, or defeat Talk about fortuitous timing. Don't blame VAR The imposition of refereeing technology has created a myth of decision-making infallibility, shown up by the video assistant referee's A-League grand final glitch, writes Richard Hinds.
Wildlife deaths on the rise Animal hospitals and carers are seeing more emaciated koalas, possums with dog bites and wallabies hit by cars than ever before. China retaliates after US slams territory warning to international airlines. Most Popular 'I am that girl':