Bitcoin rpcminer macro

It also displays a user interface Bitcoin rpcminer macro 4 after it has stolen the wallet. Download RPCMiner for free. Sirefef [ 34 ] bitcoin rpcminer macro a sophisticated, multi-component malware family that uses stealth techniques to hide itself on a compromised computer and communicate with other remote peers using a P2P protocol. Note that Bitcoin users can also store their wallet data via other means, such as through websites that store their Bitcoin wallet by sending their bitcoins to a Bitcoin address generated by the website for instance instead of keeping their wallet data on their machine.
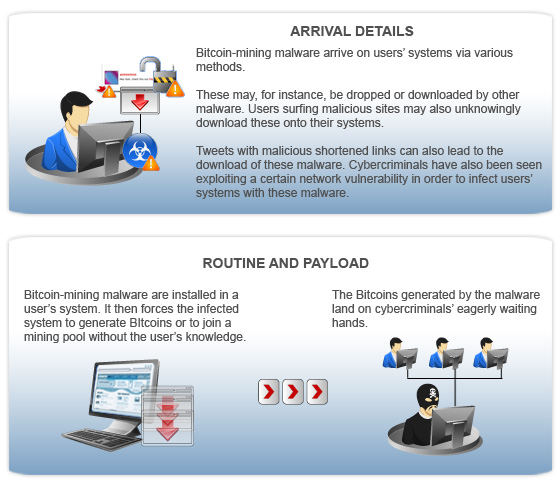
Pool mining In case of Bitcoin pool mining, you need the software to connect to your mining. The worm is programmed to launch Internet Explorer in the background and direct the browser to the Bitcoin Plus generator page, ensuring the compromised user is unaware they are generating bitcoins for the account holder through the Bitcoin Plus Java applet. Once a certain number of problems have been solved, a block of bitcoins is released. Other notable command line parameters areIfor intensity andkfor kernel. The first malicious program seen in the wild containing bitcoin-mining capabilities was discovered on 26 Juneonly a few weeks after TrojanSpy:
Bitcoin rpcminer macro bears no responsibility for the safety of the software downloaded from third party sites. What happens next is the distributed computing aspect of the Bitcoin system:. Bitcoin mining on mac os x Wikipedia bitcoin mining hardware Litecoin Open source P2P digital currency. A drawback of Bitcoin wallet theft, from a malware author's perspective, is that it may be a fruitless task since bitcoin rpcminer macro infected computer must have a Bitcoin client installed and have 'funds' in their wallet.
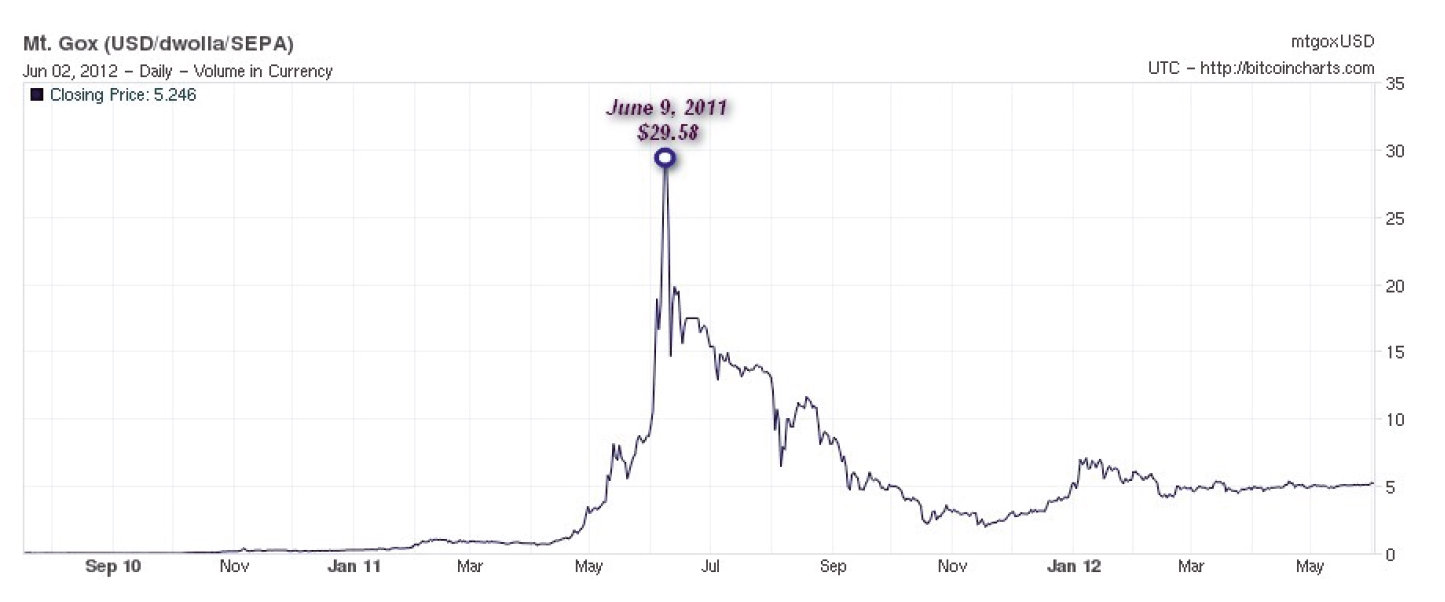
That was bitcoin rpcminer macro Juneand we've seen how volatile the value of a bitcoin has been since then. The value of the bitcoin currency can vary depending on bitcoin rpcminer macro exchange used, but the most widely used exchange, Mt. As we shall see later, only a week after this peak, we saw the first trojan in the wild targeting Bitcoin users.

The use of distributed systems is bitcoin rpcminer macro and traverses many fields, with many projects in existence that utilize this method. The miner retrieves work i. But the fact that many businesses, including online stores and retailers, are now accepting bitcoins also plays a factor in its increased usage.