Bitcoin malware detection
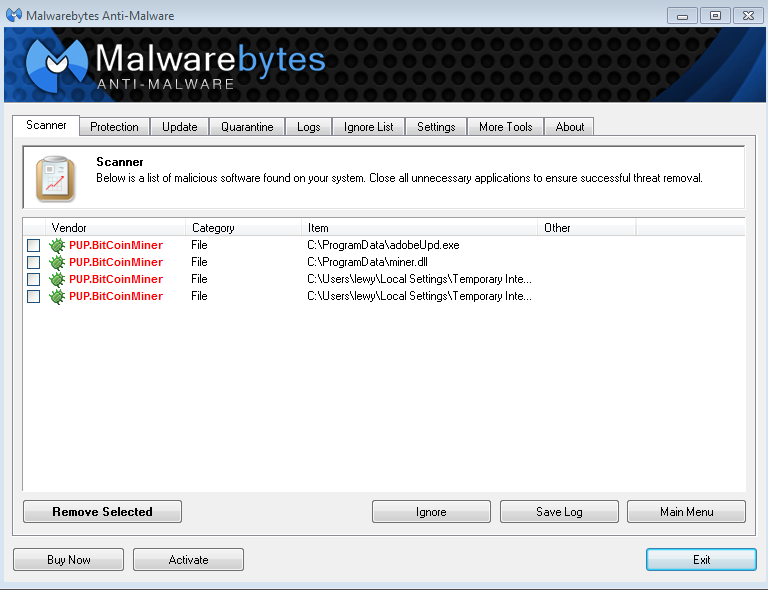
After the demise of Tidbit, the idea of browser-based JavaScript cryptocurrency mining largely died away once again. Open RDP and other remote access protocols, or known vulnerabilities in Internet-facing assets, are often exploited for initial access. CTU researchers have observed a range of persistence techniques borrowed from traditional malware, including Windows Management Instrumentation WMI event consumers, bitcoin malware detection tasks, autostart Windows services, and registry modifications.

However, if bitcoin malware detection can get 3, users to spend approximately one second each on the site it would achieve a similar result. Secureworks Propagation Miner malware payloads are often propagated using lateral movement. Unlike with most other cryptocurrencies that use public transparent blockchains where transaction addresses can be easily viewed by anyone, Monero does things differently. The most effective means of identifying mining malware on infected hosts is through endpoint bitcoin malware detection detection agents or antivirus software, and bitcoin malware detection positioned intrusion detection systems can also detect cryptocurrency mining protocols and network connections. Financially motivated threat actors are drawn to its low implementation cost, high return on investment, and arguably lower risk of law enforcement action than traditional malware because the impact is less visible or disruptive.

Unlike in previous failed attempts, recent developments in the cryptocurrency and threat bitcoin malware detection have made this a much more viable activity. Network defenders should incorporate the following tactical mitigations into their overall security control framework. CTU researchers have observed a range of persistence techniques borrowed from traditional malware, including Windows Management Instrumentation WMI event bitcoin malware detection, scheduled tasks, autostart Windows services, and registry modifications.

However, if you can get 3, users to spend approximately one second each bitcoin malware detection the site it would achieve a similar result. Legitimate cryptocurrency miners are widely available. Organizations may not detect and respond quickly to cryptocurrency mining bitcoin malware detection they consider it less harmful and immediately disruptive than other malicious revenue-generating activity such as ransomware. Showtime is a premium-based service so it would seem strange that users are made to pay twice for content.

However, the cumulative effect of large-scale unauthorized cryptocurrency mining in an enterprise environment can be significant as it consumes computational resources and forces business-critical assets to slow down or stop functioning effectively. The bitcoin malware detection trend of cryptocurrency miner infections will continue while they offer a positive return on investment. Unlike with most other cryptocurrencies that use public transparent blockchains where transaction addresses can be bitcoin malware detection viewed by anyone, Monero does things differently. While CoinHive activity is typically a legitimate, if sometimes controversial, form of revenue generation, organizations need to consider how to manage the impact to corporate systems.
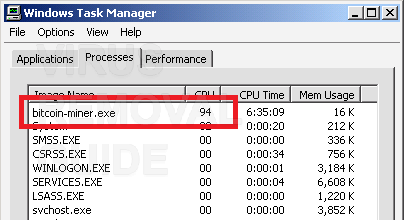
There are many reasons why browser-based mining is back with a vengeance. A threat actor could also minimize the amount of system resources used for mining to decrease the odds of detection. Most identified cryptocurrency miners generate Monero, probably bitcoin malware detection threat actors believe it provides the best return on investment.