Bitcoin cryptographic hash function examples
First is public key cryptography. When you send some bitcoins to someone, you create a message transactionattaching the new owner's public key to this amount of coins, and sign it with your private key. When this transaction is broadcast to the bitcoin network, this lets everyone know that the new owner of these coins is the owner of the new key.
Your signature on the message verifies for everyone that the message is authentic. The complete history of transactions is kept by everyone, so anyone can verify who is the current owner of any particular group of coins. This complete record of transactions is kept in the block chainwhich is a sequence of records called blocks. All computers in the network have a copy of the block chain, which they keep updated by passing along new blocks to each other.
Each block contains a group of transactions that have been sent since the previous block. In order to preserve the integrity of the block chain, each block in the chain confirms the integrity of the previous one, all the way back to the first one, the genesis block.
Record insertion is costly because each block must meet certain requirements that make it difficult to generate a valid block.
This way, no party can overwrite previous records by just forking the chain. To make generating bitcoins difficult the Hashcash cost-function is used. Hashcash is the first secure efficiently verifiable cost-function or proof-of-work function. The beauty of hashcash is that is is non-interactive and has no secret keys that have to be managed by a central server or relying party; hashcash is as a result fully distributed and infinitely scalable. In bitcoin, integrity, block-chaining, and the hashcash cost-function all use SHA as the underlying cryptographic hash function.
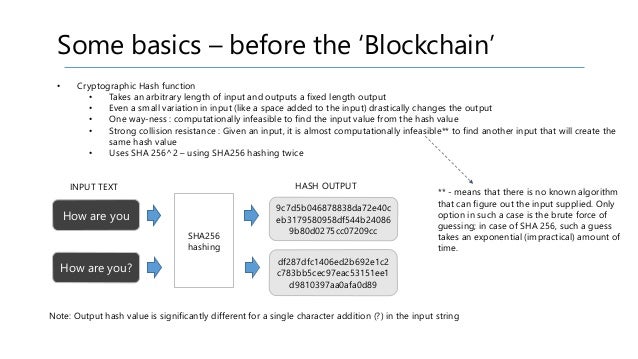
A cryptographic hash function essentially takes input data which can be of practically any size, and transforms it, in an effectively-impossible to reverse bitcoin cryptographic hash function examples to predict way, into a relatively compact string in the case of SHA the hash is 32 bytes. Making the slightest change to the input data changes its hash unpredictably, so nobody can create a different block of data that gives exactly the same hash.
Therefore, by being given a compact hash, you can confirm that it matches only a particular input datum, and in bitcoin the input data being a block-chain is significantly larger than the SHA hash.
This way, Bitcoin blocks don't have to contain serial numbers, as blocks can be identified by their hash, which serves the dual purpose bitcoin cryptographic hash function examples identification as well as integrity verification. An identification string that also provides its own integrity is called a self-certifying identifier.
The hashcash difficulty factor bitcoin cryptographic hash function examples achieved by requiring that the hash output has a number of leading zeros. Technically, to allow more fine-grained control than Hashcash number of leading 0-bits method, Bitcoin extends the hashcash solution definition by treating the hash as a large big-endian integer, and checking that the integer is below a certain threshold.
The hashcash cost-function iterates by perturbing data in the bitcoin cryptographic hash function examples by a nonce value, until the data in the block hashes to produce an integer below the threshold - which takes a lot of processing power.
This low hash value for the block serves as an easily-verifiable proof of work - every node on the network can instantly verify that the block meets the required criteria. With this framework, we are able to achieve the essential functions of the Bitcoin system. We have verifiable ownership bitcoin cryptographic hash function examples bitcoins, and a distributed database of all transactions, which prevents double spending.
We have mentioned in the previous section that adding a block to the block chain is difficult, requiring time and processing power to accomplish. The incentive to put forth this time and electricity is that the person who manages to produce a block gets a reward. This reward is two-fold. First, the block producer gets a bounty of some number of bitcoins, which is agreed-upon by the network.
Currently this bounty is 25 bitcoins; this value will halve everyblocks. Second, any transaction fees that may be present in the transactions bitcoin cryptographic hash function examples in the bitcoin cryptographic hash function examples, get claimed by the block producer.
This gives rise to the activity known as "Bitcoin mining " - using processing power to try to produce a valid block, and as a result 'mine' some bitcoins. The network rules are such that the difficulty is adjusted to keep block production to approximately 1 block per 10 minutes.
Thus, the more miners engage in the mining activity, the more bitcoin cryptographic hash function examples it becomes for each individual miner to produce a block. The higher bitcoin cryptographic hash function examples total difficulty, the harder it is for an attacker to overwrite the tip of the block chain with his own blocks which enables him to double-spend his coins.
See the weaknesses page for more details. Besides being important for maintaining the transaction database, mining is also the mechanism by which bitcoins get created and distributed among the people in the bitcoin economy.
The network rules are such that over the next hundred years, give or take a few decades, a total of 21 million bitcoins will be created. See Controlled Currency Supply. Rather than dropping money out of a helicopter, the bitcoins are awarded to those who contribute to the network by creating blocks in the block chain.
The block chain is a common ledger shared by all Bitcoin nodes which details the owner of each bitcoin, or fraction thereof. Unlike conventional banking systems, there is no central place where this ledger of transactions is stored. This is accomplished through bitcoin cryptographic hash function examples broadcasting of small pieces "blocks"each bitcoin cryptographic hash function examples that it is a continuation of a previous block.
It is possible for the block chain to split; that is, it is possible for two blocks to both point to the same parent block and contain some, but not all, of the same transactions. When this happens, each computer in the network must decide for itself which branch bitcoin cryptographic hash function examples the "correct" one that should be accepted and extended further. The rule in this case is to accept the "longest" valid branch.
Choose from the branches of blocks that you have received, the path, bitcoin cryptographic hash function examples total "difficulty" of which is the highest. This is the sequence of blocks that is assumed to have required the most work CPU time to generate.
For Bitcoin, this will be the "true" order of events, and this is what it will take into account when calculating the balance to show to the user. It is still possible that, as new blocks are constantly being generated, at some later time, some other branch will become the longest branch. However, it takes significant effort to extend a branch, and nodes work to extend the branch that they have received and accepted bitcoin cryptographic hash function examples is normally the longest one.
So, the longer this branch becomes compared to the second-longest branch, the more effort it will take for the second-longest branch to catch up and overcome the first in length.
Also, the more nodes in the network hear about the longest branch, the more unlikely it becomes for other branches to be extended the next time a block is generated, since the nodes will accept the longest chain. Therefore, the more time a transaction has been part of the longest block chain, the more likely it is to remain part of the chain indefinitely.
This is what makes transactions non-reversible and this is what prevents people from double-spending their coins. When the block chain after the transaction has become long enough, it becomes near-impossible for another branch to overcome it, and so people can start accepting the transaction as true.
This is why 'blocks' also serve as 'confirmations' for a transaction. Even if another branch does overcome the one with the transaction, most of the blocks will have been generated by people who have no affiliation with the sender of the coins, as a large number of people are working to generate blocks. Since transactions are broadcasted to all nodes in the network, these blocks are just as likely to contain the transaction as the blocks in the previously-accepted branch. Bitcoin relies on the fact that no single entity can control most of the CPU power on the network for any significant length of time, since, if they could, they would be able to extend any branch of the tree they chose, and faster than any other branch can bitcoin cryptographic hash function examples extended, making it the longest branch, and then permanently controlling which transactions appear in it.
This article requires cleanup to meet the Bitcoin Wiki's quality standards. This page explains the basic framework of Bitcoin's functionality. Retrieved from " https: Navigation menu Personal tools Create account Log in.
Views Read View source View history. Sister projects Essays Source. This page was last edited on 4 Februaryat Content is available under Creative Commons Attribution 3. Privacy policy About Bitcoin Wiki Disclaimers.

In Part 1 we took a look at the incentives involved in Bitcoin mining and how they bitcoin cryptographic hash function examples used guarantee a single transaction history needed to prevent bitcoins from being double spent.
In this post we will take more a technical look at the cryptography involved and how it is used to secure the network. As I said previously, Bitcoin is very accessible. Before moving forward we should take a moment to learn about hash functions since they are used all throughout the Bitcoin protocol. To put it simply, bitcoin cryptographic hash function examples hash function is just a mathematical algorithm that takes an input and turns it into an output.
For example, suppose we have an algorithm which just adds all the digits in the input string together. If our input is we would get an output of However, there are certain properties of really good hash functions that make them suitable to use in cryptography. Keep these properties in mind as they are vital to the operation of the Bitcoin protocol. The output should be the same length regardless of whether the input has 10 characters or 10 thousand characters.
A tiny change in the input should produce an entirely different output that in no way relates to the original input.
You might wonder how we can trust something that came bitcoin cryptographic hash function examples the NSA. The consensus is that they are secure. Now that we have the preliminaries out of the way we can start focusing in on the protocol. If you read Part 1 you will recall that all Bitcoin transactions are relayed to each of the peers in the network.
The first step in the process is to hash each transaction in the memory pool using SHA The raw transaction data may look something like this:. These hashes are then organized into something called a Merkle Tree or hash tree. The hashes of the transactions are organized into pairs of twos, concatenated together, bitcoin cryptographic hash function examples hashed again. The same is done to each set of outputs until something like a tree is formed or an NCAA bracket.
In the above example there are only four transactions tx stands for transaction. A real block will contain hundreds of transactions so the bracket tree will be much larger. The hash at the very top of the tree is called the Merkle Root. The block header will look something like this:.
Now having done all this can we go ahead and relay the block to the rest of the network? If you recall the last post, the answer is no. We still need to produce a valid proof of work. The output must be less than the specified number.
Another way bitcoin cryptographic hash function examples saying this is that the hash of the block header must start with a certain number of zeros. For example a valid hash may look like this: Any block whose header does not produce a hash that is less than the target value will be rejected by the network. The target value is adjusted by the protocol every two weeks to try to maintain an average block time of 10 minutes.
This is where the nonce comes in. The nonce is simply a random number that is added to the block header for no other reason than to give us something to increment bitcoin cryptographic hash function examples an attempt to produce a valid hash. If your first attempt at hashing the header produces an invalid hash, you just add one to the nonce and rehash the bitcoin cryptographic hash function examples then check to see if that hash is valid.
This is Bitcoin mining in bitcoin cryptographic hash function examples nutshell. This is essentially what Bitcoin mining is, just bitcoin cryptographic hash function examples the block header, over, and over, and over, and over, until one miner in the network eventually produces a valid hash. When he does, he relays bitcoin cryptographic hash function examples block to the rest of the network. If so, they add the bitcoin cryptographic hash function examples to their local copy of the block chain and move on to finding the next block.
However, the more hashes that you can perform per second, the greater the probability that you will mine a block and earn the block reward.
CPU mining quickly gave way to GPU mining graphics processing units which proved much more efficient bitcoin cryptographic hash function examples calculating hash functions. Basically, these are purpose built computer chips that are designed to perform SHA calculations and do nothing else.
At present, the total hashing power in the network is about terrahashs per second and closing in on one petahash per second. Because each miner is sending these 25 bitcoins to his own address, the first transaction in each bitcoin cryptographic hash function examples will differ from miner to miner.
Now remember the properties of a cryptographic hash function? If an input changes even in the slightest, the entire output changes. Since the hash of the coinbase transaction at the base of the hash tree is different for each miner, the entire hash tree including the Merkle root will be different for each miner.
That means the nonce that is needed to produce a valid block will also be different for each miner. This is the reason why the Merkle tree is employed after all. Any change to a single transaction will cause an avalanche up the hash tree that will ultimately cause the hash of the block to change. If an attacker wants to alter or remove a transaction that is already in the block chain, the alteration will cause the hash of the transaction to change and spark off changes all the way up the hash tree to the Merkle Root.
Given the probabilities, it is unlikely a header with the new Merkle Root will produce a valid hash the proof of bitcoin cryptographic hash function examples. Hence, the attacker will need to rehash the entire block header and spend a ton of time finding the correct nonce. But suppose he does this, can he just relay his fraudulent block to the network and hope that miners will replace the old block with his new one or, more realistically, that new users will download his fraudulent block?
The reason is because the hash of each block is included in the header of the next block. If the attacker rehashes block numberthis will cause the header of block to change, requiring that block to be rehashed as well.
A change to the hash of block will cause the header of block to change and so on all the way through the block chain. Any attempt to alter a transaction already in the block chain requires not only the rehashing of the block containing the transaction, but all other subsequent blocks as well. Depending on how deep in the chain the transaction is, it could take a single attacker weeks, months, or years, to rehash the rest of the block chain.
The only exception to the above rule is if the attacker simply gets lucky. As we noted, it takes the entire network an average of 10 minutes bitcoin cryptographic hash function examples find a bitcoin cryptographic hash function examples block. The deeper a transaction is in the block chain, however, the more times in row the attacker would need to get lucky and mine a block before the rest of the network to extend his chain longer than the main chain.
From a probability standpoint, the chances of such an attack succeeding decrease exponentially with each subsequent block. In the original white paper Satoshi Nakamoto calculated the probabilities that an attacker could get lucky and pull off a double spend.
In the following table q is the percentage of the network controlled by the attacker, P is the probability an attacker could get lucky and override z number of blocks. Which is usually why it is recommended that if you are selling something expensive, you should wait until your transaction is six blocks deep six confirmations in Bitcoin lingo before actually handing over the merchandise.
This post got long in a hurry. Hope you enjoyed these posts and I hope you learned something. I found your post comments while searching Google. It is very relevant information. Regularly I bitcoin cryptographic hash function examples not make posts on blogs, but I have to say that this posting really forced me to do so. Really fantastic and I will be coming back for more information at your site and revisit it! I still have one question though: Smart Contracts Great Wall of Numbers.
Part 2 bitcoin cryptographic hash function examples Mechanics … Bitcoin. For the hash chaining, does it mean if somebody get one valid hash, I need to update and download it and re-calculate based on his block? Or can I make a new branch based on previous block? Bitcoin Online resources collected The Bitcoin Journey How Cryptocurrencies Work Bitcoin Getter. Bitcoin has seen rapid increases during the last year and there are now those who are claiming that the bubble is soon to burst and Bitcoin crumble.
Those of us continue believe in the idea of a user owned system away from the reach of the banks. We do not believe that the currency is finished. We shall be staying with Bitcoin and I am quite confident bitcoin cryptographic hash function examples it will continue to rise more rapidly than before.
Bitcoin Frenzy — Is it the next gold or just a bubble? How Cryptocurrencies Work - Cryptocurrency How Cryptocurrencies Work — Bitcoin Support. Thanks for a great article. How then does the miner broadcast that to the rest of the network to get consensus on the work if his nonce is unique from what another miner would have theoretically found?
Cryptocurrency trading is becoming a profession — The Glimpse. How Cryptocurrencies Work — Bitcoin Supports. How Cryptocurrencies Work — Blok Chn.
You are commenting using your WordPress. You are commenting using your Twitter account. You are commenting using your Facebook account. Notify me of new comments via email. Notify me of new posts via email. Cryptographic Hash Functions Before moving forward we should take a moment to learn about hash functions since they are used all throughout the Bitcoin protocol.
It should be very easy to compute an output for any given input, however it should be impossible given current knowledge of mathematics and the state of computers to compute the input for a given output even while knowing the mathematical algorithm. In this case there are many possible inputs that could add up to 10 55, etc.

Beta3 New API Parallel Queue Request Bitcoin cryptographic hash function examples Panel For Each Markets Sort Open Market in Lexicographic Order Markets Tab change dynamically colour depending by the algoritm Status. This notwithstanding the recent furore which saw BTC supporters threaten, and subsequently drop, a lawsuit against BCH-proponent Roger Verвs site bitcoin. It is decorated with attractive pavilions, bridges, ponds and plants. Now when you have a bot net that suddenly has a lot of bitcoin cryptographic hash function examples, what would you do with them.
They are good for trading, but if you need to park your bitcoins, either use a mobile-based wallet such as MyCelium, or buy a hardware wallet like LedgerWallet or Trezor.